Software Defined Vehicles (SDV) represent a fundamental shift in automotive design where software and centralized compute define vehicle capability more than hardware modules. Functional Safety in SDVs are expanding the role of software in vehicles from convenience features to core safety functions.
The automotive software and electronics market is projected to reach roughly USD 462 billion by 2030. Functional safety regimes originally written for distributed electronic control unit-based vehicles must evolve to cover centralized compute, zonal architectures, continuous over the air updates and large software stacks.
Key standards such as ISO 26262 remain central while regulatory frameworks including UNECE rules for software update management are becoming mandatory.
Table of Contents
What is Functional Safety?
Functional safety ensures that electrical and electronic systems operate correctly and predictably even when hardware or software faults occur. The ISO 26262 framework governs this process by defining activities such as hazard analysis, Automotive Safety Integrity Level classification, fault tolerant architectural design and rigorous verification.
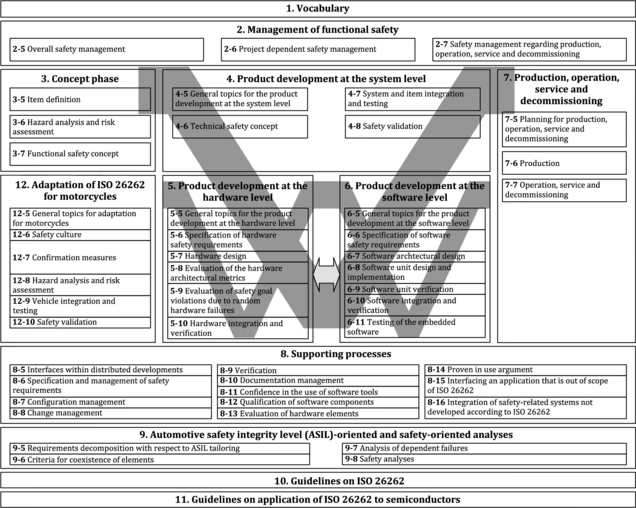
For example, a braking control system must detect sensor faults, switch to redundant data sources when available and still maintain a controlled deceleration that keeps the vehicle stable.
In modern SDVs this extends to managing complex interactions in centralized compute domains where timing, isolation and resource contention can affect multiple safety relevant functions simultaneously.
Continuous validation through hardware in the loop testing, virtual simulation and over the air update assessment ensures that incremental software changes do not introduce new hazards, and engineers now adapt ISO 26262 practices to fit centralized software platforms, multi core safety domains and continuous update pipelines.
Changing vehicle software
Modern vehicles now include orders of magnitude more software than a decade ago. Estimates show average lines of code per vehicle roughly doubled between 2015 and 2020 and could reach hundreds of millions of lines of code in the near term.
This software growth increases complexity and the probability that software faults can produce safety critical failures unless managed with strong functional safety processes.

The challenge becomes even more visible in domains such as advanced driver assistance where perception pipelines can involve tens of thousands of interconnected functions that must all execute deterministically.
The integration of high resolution camera stacks with real time sensor fusion often forces engineers to verify thousands of software variants, which magnifies failure modes that earlier remained contained within small embedded modules.
The Toyota Arene platform serves as a concrete industry effort to unify software stacks and enable extensive over the air capabilities, which forces manufacturers to prove that updates distributed across millions of vehicles maintain consistent timing and determinism in safety relevant functions.
High level program decisions by major manufacturers, including cases where they re scoped or cancelled centralized software programs, demonstrate the real world difficulty of building scalable platforms that meet both commercial and safety expectations.
Compartmentalized ECUs to centralized compute
Functional Safety in SDVs becomes significantly more complex as vehicles adopt centralized high performance compute platforms and zonal electronic and electrical architectures. This consolidation changes failure modes from isolated module faults to complex cross function interactions and software integration faults at scale.
Centralized platforms also change the update model because software updates can modify entire functions, which requires engineers to maintain continuous safety assurance rather than rely on a onetime type approval.
This concentration of compute power means that a timing error in a shared scheduler or a memory contention issue inside a multicore processor can simultaneously affect perception, actuation and diagnostic functions, which was far less likely in separated controller environments.
When radar processing, camera processing and path planning share the same compute domain, an unexpected increase in computational load from one pipeline can delay safety critical tasks in another, requiring advanced real time partitioning and continuous performance monitoring to maintain functional safety in SDVs.
UNECE for software update and Cybersecurity
Regulatory frameworks are adapting. UNECE Regulation 156 requires manufacturers to demonstrate safe and managed procedures for software updates on vehicles. In parallel, WP 29 cybersecurity and cyber management system rules require processes to address security risks that can impact safety.
Together these frameworks formalize continuous safety and security management across the vehicle lifecycle.

These requirements mean that every update must include traceable testing evidence, integrity checks and rollback capabilities so that a malfunctioning software package cannot compromise functions such as braking or lane keeping.
For example, if a camera perception module receives an update that changes object classification logic, the manufacturer must show through simulation and controlled field testing that the new model does not create latent hazards under rare environmental conditions.
Software Complexity, Continuous Updates and Scalable Verification
Large code bases and frequent updates make exhaustive testing impractical, and the verification challenge is to provide high assurance that a software update does not introduce or reintroduce hazardous behavior.
Achieving this requires a combination of formal methods, automated regression testing, hardware in the loop setups and virtualized validation environments capable of running millions of test cases across numerous software variants. As vehicles become continuously updateable, the safety case transitions from a static approval document to a dynamic evidence set that must evolve with every new software release.
Manufacturers must therefore demonstrate that their update processes include thorough risk analysis, reproducible regression testing, rollback capability and controlled deployment aligned with Automotive Safety Integrity Level classifications.
Partitioning & Supply Chain Integrity in Centralized Compute
On a single high performance compute platform, safety critical and non-safety critical software often must coexist, which makes robust temporal and spatial partitioning, mixed criticality operating systems and hypervisor level isolation essential to ensure that faults in non-safety functions cannot disrupt real time safety functions.
Architectural decisions must clearly demonstrate how isolation strategies satisfy the Automotive Safety Integrity Level assigned to each function, especially when multiple perception, control and infotainment pipelines share the same compute resources.
At the same time, the growing reliance on tiered suppliers introduces additional complexity because middleware, libraries and complete operating environments sourced from third parties can propagate latent vulnerabilities or functional faults into safety critical paths.
This has elevated the importance of strong supplier management practices, software bills of materials, automated vulnerability scanning and contractual safety requirements that bind suppliers to traceable development and assurance processes.
Final Thoughts
Functional safety in SDVs is not a simple extension of previous practices. The industry must move from static certification mindsets to continuous evidence driven assurance that spans software development, update management and supplier ecosystems.
Standards such as ISO 26262 remain foundational while regulatory frameworks like UNECE Regulation 156 change how manufacturers must demonstrate safety across the operational lifecycle.
Investments in continuous verification, partitioning technologies and integrated security and safety processes are the practical steps that will allow the promise of Software Defined Vehicles to materialize without compromising safety.


